TeamPCP, operating under aliases including PCPcat, ShellForce, and DeadCatx3, emerged in late 2025 as a cloud-native cybercrime operation that transforms misconfigured infrastructure into automated attack platforms.
Unlike traditional malware groups, this threat actor doesn’t break into systems they walk through doors left open by exposed Docker APIs, Kubernetes clusters, Ray dashboards, Redis servers, and React2Shell-vulnerable applications.
The operation peaked dramatically around Christmas Day 2025, targeting cloud environments through a worm-driven exploitation strategy.
Researchers identified 185 compromised servers running attacker-deployed containers with standardized command patterns, establishing a reliable fingerprint of PCPcat’s automated deployment pipeline.
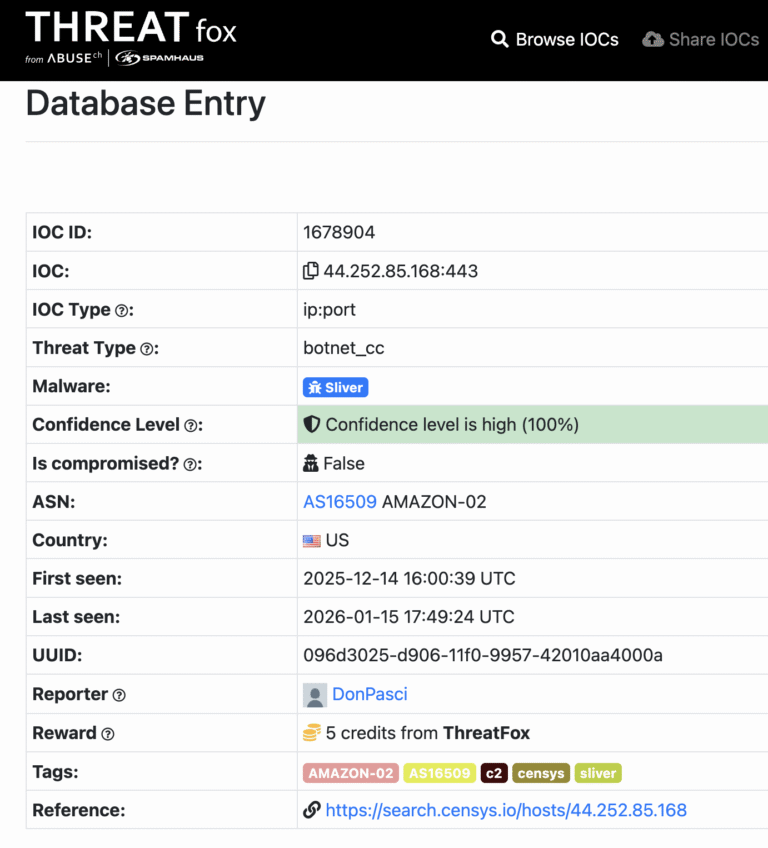
The campaign’s primary command-and-control infrastructure centered on IP address 67.217.57.240, which appeared on 182 compromised hosts, with a secondary node at 44.252.85.168 observed on three additional victim servers.
Security teams reported that the group compromised approximately 60,000 servers worldwide within just 48 hours, demonstrating unprecedented automation and scale.
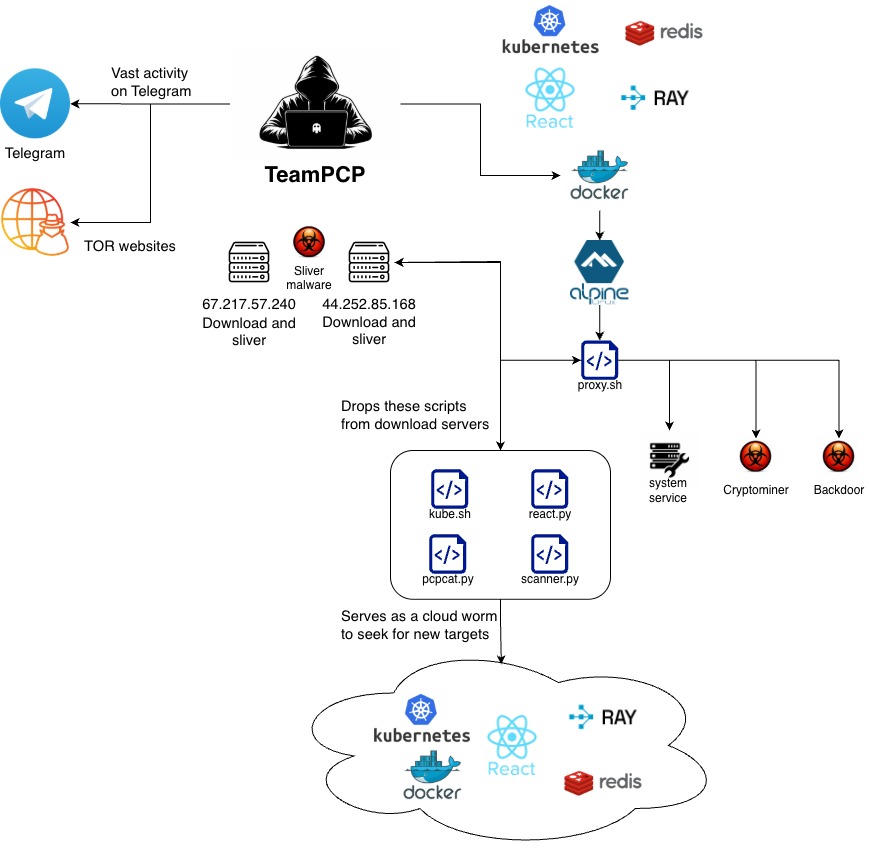
The attack chain begins with scanning for vulnerable services, then deploys proxy scripts that install tunneling utilities, additional scanners, and persistence mechanisms that survive system reboots.
Industrialized Exploitation, Not Innovation
What distinguishes TeamPCP is not technical sophistication but operational industrialization. The group leverages well-known vulnerabilities and lightly modified open-source tools rather than developing novel exploits.
Their weaponized arsenal includes React2Shell (CVE-2025-29927) for remote code execution against Next.js applications, exposed orchestration APIs for container deployment, and standard malware like XMRig for cryptocurrency mining, Sliver for command-and-control, and FRPS/gost for tunneling.
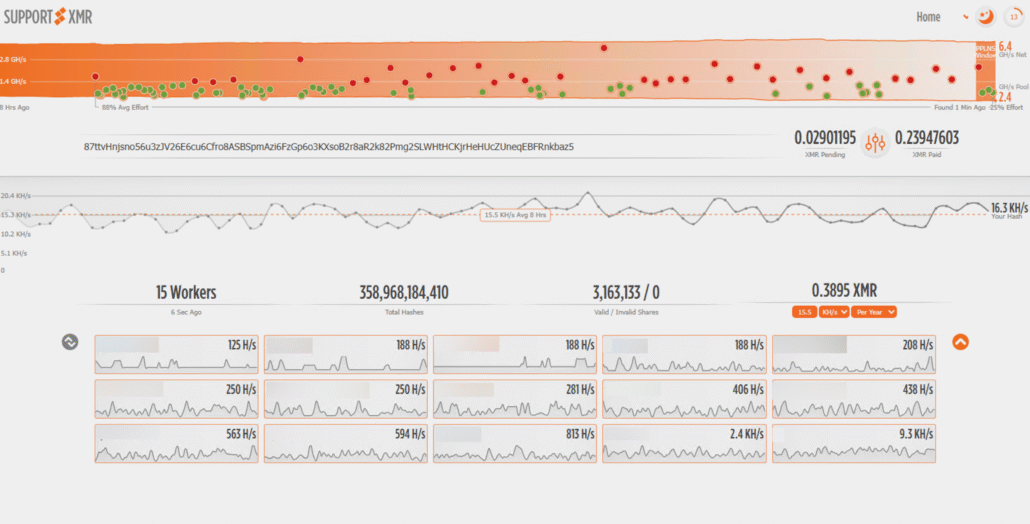
The React2Shell vulnerability proved particularly devastating, with multiple threat actors, including Chinese state-nexus groups, exploiting it within hours of public disclosure in December 2025.
TeamPCP’s automated exploitation scripts systematically harvest environment variables, SSH keys, Git credentials, and cloud provider secrets from compromised applications.
TeamPCP operates as a hybrid cybercrime platform with diverse revenue streams. Compromised infrastructure serves simultaneously as cryptocurrency mining nodes, proxy and scanning infrastructure, data exfiltration platforms, and ransomware deployment targets.
The group’s Telegram channels particularly TeamPCP with nearly 700 members and ShellForce for data leaks showcase stolen databases from victims across Canada, Serbia, South Korea, the United Arab Emirates, and the United States.
Analysis reveals that 97% of compromised servers run on Azure (61%) and AWS (36%), confirming the group’s cloud-first targeting strategy.
Leaked datasets include personally identifiable information, CVs, employment records, and business data raw material for spear-phishing, account takeover operations, and identity fraud.
In one notable breach, ShellForce released 2.3 million candidate resume records from Vietnamese recruitment platform JobsGO in January 2026.
Cloud-Native Persistence
When TeamPCP compromises Kubernetes environments, the operation escalates dramatically. Custom scripts perform environment fingerprinting to detect Kubernetes clusters, then deploy cluster-specific payloads that harvest credentials, enumerate pods and namespaces, and execute remote commands across all accessible containers.
The malware establishes persistent backdoors by deploying privileged DaemonSets that mount host filesystems, effectively converting entire clusters into self-propagating scanning infrastructure.
In threat intel reports, “Sliver” usually indicates post-exploitation activity and an operator-controlled foothold rather than an initial infection vector.
This worm-like behavior ensures that a single misconfigured Docker API or exposed Kubernetes endpoint provides an entry point into an entire cloud environment.
Each compromised workload becomes a scanner searching for additional vulnerable services, creating exponential growth potential.
TeamPCP’s success stems from fundamental security gaps rather than zero-day exploits. Organizations must harden cloud control planes by requiring authentication on Docker APIs, implementing network policies for Kubernetes, and enforcing runtime security controls that prevent privileged containers and host filesystem mounts.
Detection strategies should monitor for unauthorized container deployments, unexpected Kubernetes DaemonSets, high CPU usage from cryptominers, and outbound connections to known malicious infrastructure.
The threat demonstrates that cloud security cannot rely on traditional endpoint protection alone.
When TeamPCP is detected, organizations must assume cluster-wide compromise and implement immediate containment, credential rotation, and infrastructure rebuilding from clean baselines.
As long as orchestration APIs remain exposed and secrets leak into container images, threat actors will continue industrializing cloud infrastructure into criminal platforms.