ClickFix is being weaponized against macOS developers by turning a trusted Homebrew workflow into a stealthy delivery channel for a new infostealer dubbed Cuckoo Stealer.
The campaign shows how attackers can skip exploit chains entirely and instead rely on users to run the payload for them.
The attack starts with typosquatted domains that closely mimic the official Homebrew site, including homabrews[.]org and other lookalike hostnames served from shared infrastructure at 5.255.123[.]244.
These pages are near-perfect clones of brew.sh, copying layout, styling, and language options so that only the URL bar betrays the fraud.
At the center of the page is a familiar “install Homebrew” command and a “Copy” button that silently places a malicious curl | bash string onto the clipboard.
The only visible change is the download location. Instead of fetching the installer from raw.githubusercontent.com, the command points to raw. homabrews[.]org, which is structured to imitate GitHub’s raw content endpoint.
The investigation began with a single domain ClickFix first gained traction in 2024 as a deceptive execution method that abused familiar UI elements to trick users into running malware.
Within 24 hours of registration, our phishing detection systems had already flagged the domain three separate times between January 14 and January 25, 2026.
![Domain registration details for homabrews[.]org in Hunt showing high-risk assessment and registration through NameCheap (Source : Hunt.io).](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/2-2026/Fake+Homebrew+Typosquats+Used+to+Deliver+Cuckoo+Stealer+via+ClickFix+-+figure+1.png)
Because developers are conditioned to paste curl -fsSL commands into Terminal for Homebrew and similar tools, many victims execute the chain without inspecting the domain.
Credential-Harvesting Loader
Once run, the script downloads what appears to be the legitimate Homebrew installer but with malicious code injected at selected points.
Before doing anything obviously suspicious, the script enters a password-harvesting loop that repeatedly prompts the user for their macOS password and validates it using dscl authonly, reproducing the same “Sorry, try again.” flow users expect from sudo.
![Fake Homebrew installation page on homabrews[.]org showing near-perfect replication of the legitimate brew.sh website (Source : Hunt.io).](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/2-2026/Fake+Homebrew+Typosquats+Used+to+Deliver+Cuckoo+Stealer+via+ClickFix+-+figure+6.png)
With a working password captured, the loader retrieves a secondary binary (brew_agent) to /tmp from the typosquatted infrastructure, passing the Base64‑encoded credential as an argument.
The binary then removes quarantine attributes via xattr to avoid Gatekeeper prompts and establishes user‑level persistence via a LaunchAgent masquerading as a Homebrew updater (for example, com.homebrew.brewupdater.plist).
By keeping everything in the context of normal developer operations, the execution chain blends into expected macOS behavior.
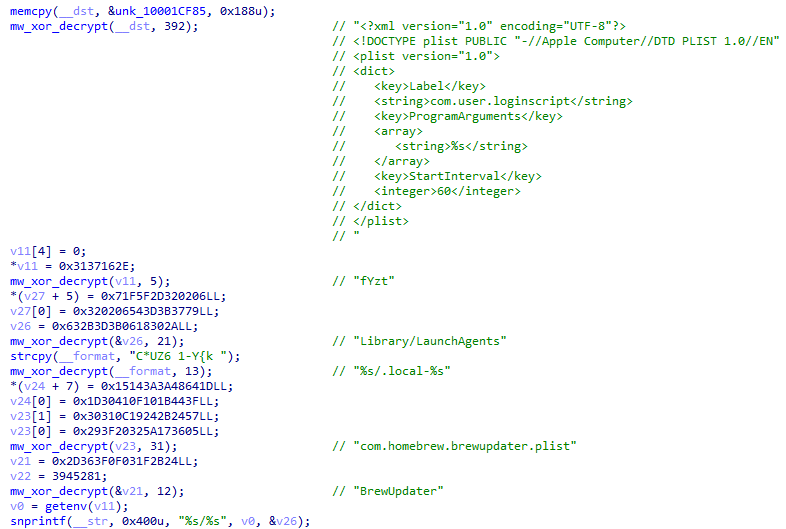
The second-stage, Cuckoo Stealer, functions as both a macOS infostealer and remote access trojan.
It initializes an HTTPS-based command-and-control channel with encrypted communications and uses a custom protocol to receive commands such as shell execution, data exfiltration, and self-removal.
Locale checks are used to avoid systems configured for certain CIS-region languages, a pattern seen in other financially motivated malware families.
Data collection is wide-ranging and tuned for high-value theft at scale. The malware targets browser passwords, cookies, and session tokens, macOS Keychain material, Apple Notes content, Discord and Telegram session data, VPN and FTP configuration files, Steam session files, and a long list of desktop and node-based cryptocurrency wallets.
It walks predefined directories for Bitcoin, Monero, Electrum, Exodus, and many other wallet implementations, staging wallet.dat files, keystores, and configuration JSON for exfiltration.
Additional modules capture silent screenshots and use separate channels to browse and steal files from Desktop and Documents while muting system audio to reduce user awareness.
Broader ClickFix Trend
The cluster anchored on homabrews[.]org is part of a larger ClickFix attack delivery pattern rather than an isolated fake Homebrew site.
SQLite database contains all of the user’s notes, which may include sensitive information such as passwords, personal data, financial details, or confidential business information.
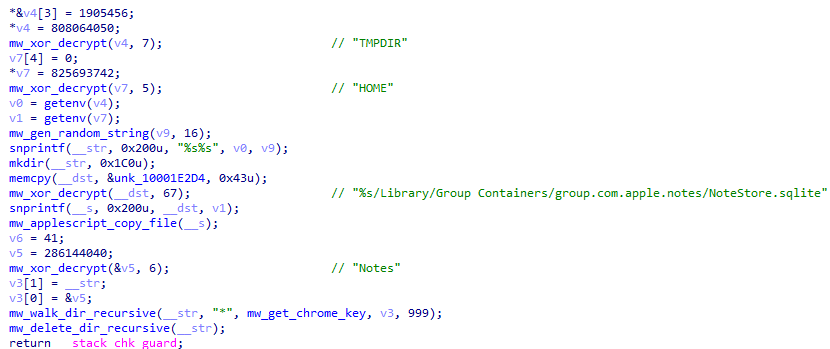
By pivoting off the shared IP and behavioral traits, researchers identified multiple typosquats and similar macOS‑focused pages abusing the copy‑and‑paste install pattern.
HuntSQL™ queries that looked for curl -fsSL, /install.sh, and “Copy to clipboard” elements across crawled pages surfaced dozens of related terminal‑phishing sites, including ones spoofing additional tools and services used by developers.
For defenders, the campaign underscores that training macOS users to “paste this command into Terminal” has become an attack surface in its own right.
Blocking known typosquats, monitoring for unapproved raw content domains in curl commands, and inspecting LaunchAgent entries that mimic popular developer tools are now essential controls against ClickFix-style operations delivering Cuckoo Stealer and similar macOS malware.
Indicators of Compromise
File Indicators
| Type | Value |
|---|---|
| loader | f985cd667c77e7d99c1ac2ea9cb0861ded15e1c2d44e480cbd178ca8b2caae42 |
| cuckoo | 545dd5cba264bf242bc837330ca34247e202f7ac25f03eec63bf5842357519f1 |
Network Indicators
| Type | Indicator | Notes |
|---|---|---|
| Domain | homabrews[.]org | Primary C2 domain |
| Domain | raw.brewsh.cx | Typosquat variant |
| Domain | braw.sh | Typosquat variant |
| Domain | brewsh.cx | Typosquat variant |
| Domain | brew.lat | Typosquat variant |
| Domain | brew.pages.dev | Typosquat variant |
| IP Address | 5.255.123[.]244 | Shared C2 infrastructure |